Jan 29, 2024
|
Product & Engineering
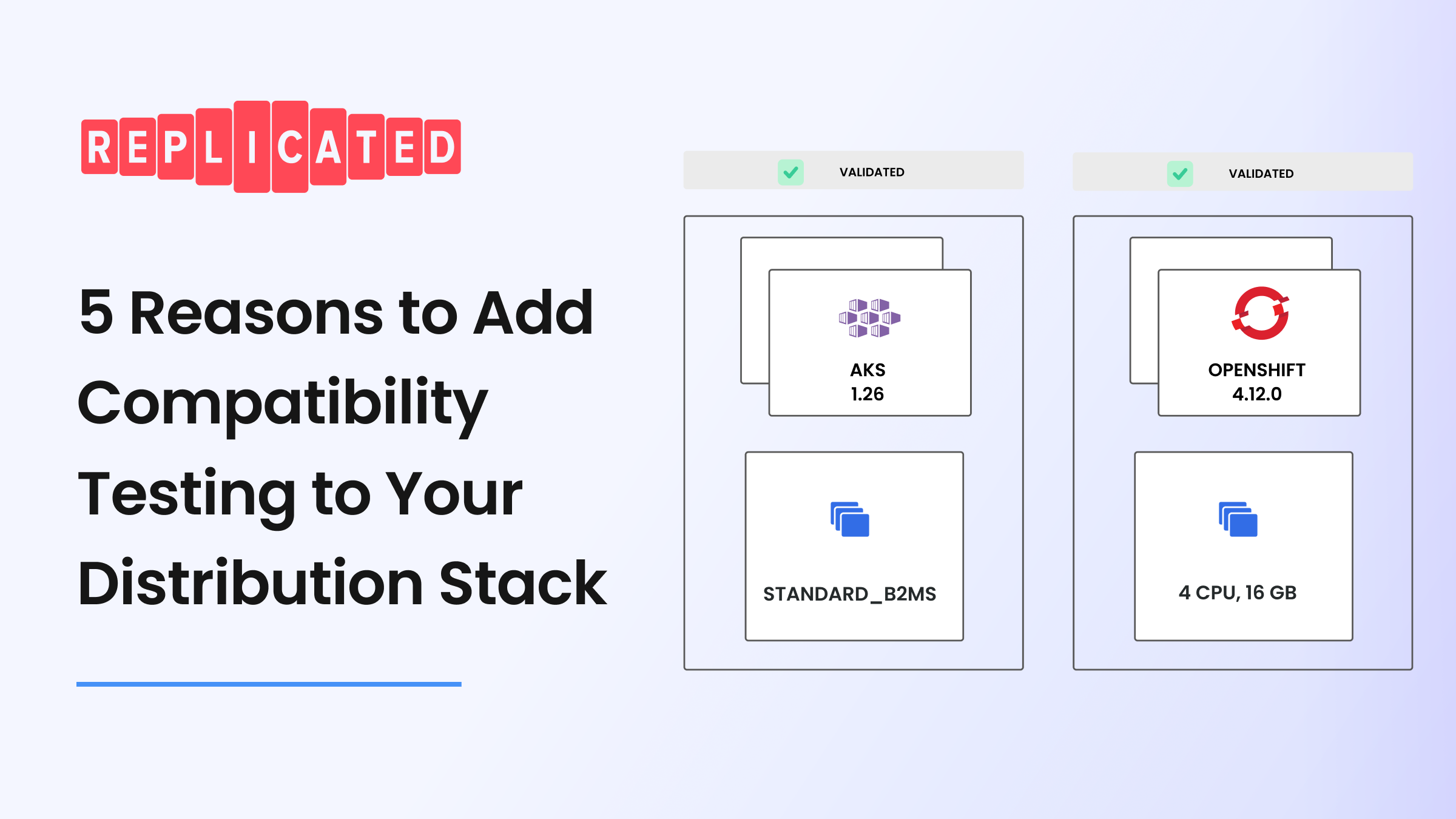
5 Reasons to Add Compatibility Testing To Your Distribution Stack
Compatibility Testing — or testing that your application can be successfully installed on unique combinations of Kubernetes distributions (Openshift, EKS, AKS, GKE, K3s, etc.), versions, and configurations — is a relatively new concept in software distribution. Can you imagine a world where you can be confident that every new customer, and every new release, goes smoothly every time? Compatibility Testing can make that happen.